The convenience and flexibility of WiFi networks make them a logical choice when providing Internet access for your home or business. There are a few issues that come along with the mobility that a WiFi network furnishes its users. They are:
Reliability
An Internet connection made with an Ethernet cable is more reliable than a connection made through WiFi. If you use WiFi at all, you have probably experienced the frustration of suddenly losing connectivity. This happens much more frequently with WiFi networks than on a cabled network.
Security
Perhaps the most troubling aspect of using WiFi networks it the security risks posed by a WiFi password hack. If an intruder was compromising your cabled network, there would be physical signs of the unauthorized access. If someone were trying to hack your WiFi password, there is a good chance you would never be aware that an attempt was made. An unscrupulous individual who understood how to hack WiFi passwords could be using your network to enact their own Internet access or gain entry into your network and electronic resources.
Protecting Yourself From a WiFi Hack
We believe that the best way to protect yourself against an intruder who wants to hack your WiFi is to know how to hack a WiFi password yourself. We are going to present a method to do just that by using your Mac computer and a freeware application called
KisMAC.
We will be giving you a step-by-step overview of the steps required to use this method and will essentially show you how to hack into WiFi. We are not presenting this information with the intention of allowing others to hack into your Wifi. If that was their intention, there are plenty of other sites that will teach them what they want to know. Our aim is to show that it is feasible that your network could be under attack at this moment without any indication that someone is trying to hack your access password.
It’s better to be armed with this knowledge than to pretend there are no potential dangers inherent in having a wireless network. So let’s take a look at how to hack into WiFi using some simple tools.
How to Hack WiFi Passwords
There are three popular security protocols that can be used to secure your wireless network. They are WEP, WPA, and WPA2. Wired Equivalent Privacy (WEP) is the weakest of the protocols. WiFi Protected Access (WPA) is stronger, followed by WPA2. All of these methods of securing a wireless network can be subverted using the tools we will describe below.
We again want to emphasize that this information is to inform individuals or network administrators regarding the potential that the security of their wireless network can be compromised. Please don’t take our explanation of how to hack WiFi networks as an invitation to attack nearby targets. To do so is a violation of privacy and can lead to criminal charges.
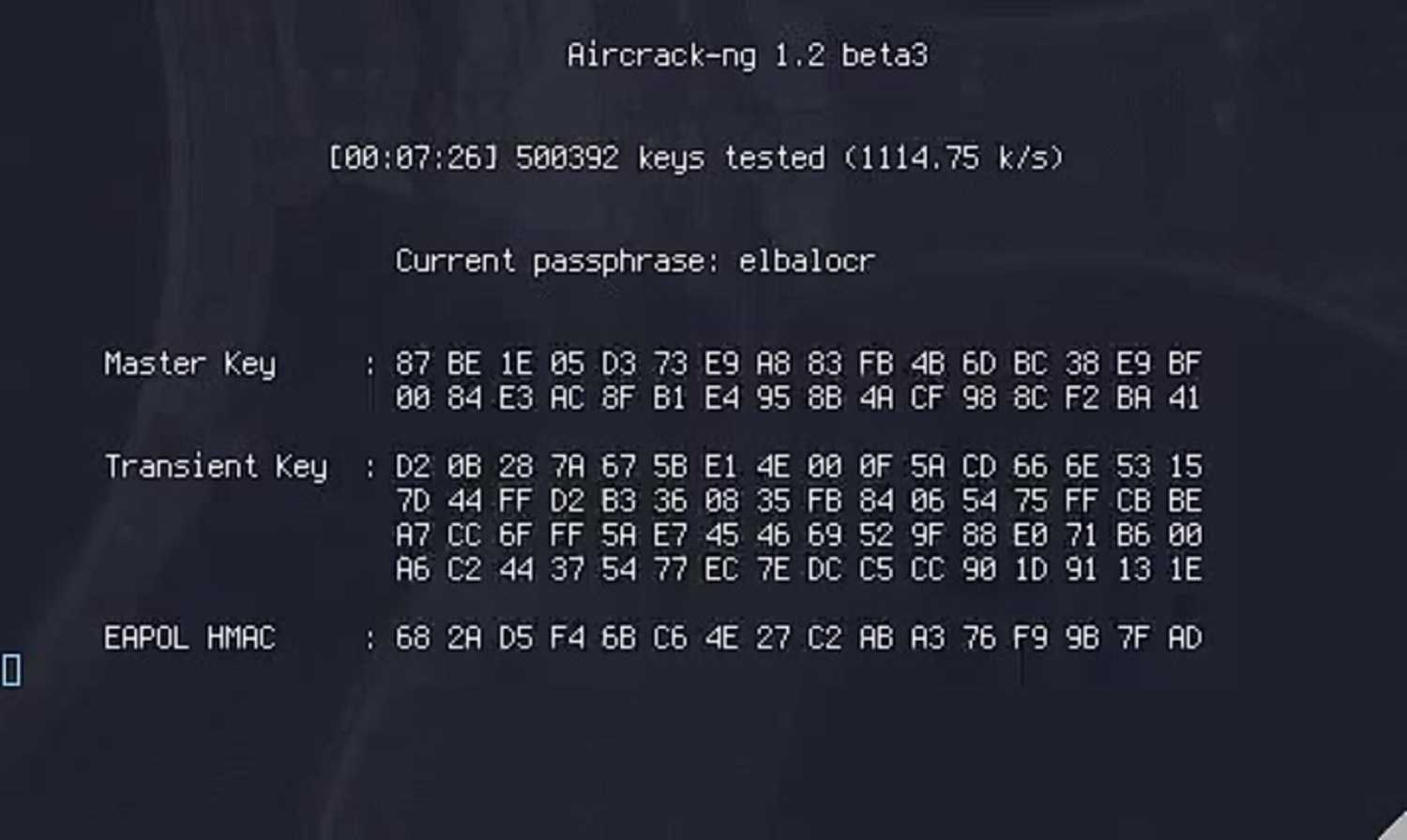
To break into a secured wireless network you need to know the password. If you don’t have the password, you need to use a method known as a “brute force” attack in order to obtain access to the network. This type of attack is very time-consuming and it is not guaranteed to work.
It preys on the fact that many wireless routers and networks are protected by very weak passwords. In some cases, there is no password or the user simply relies on the default, which can easily be found by knowing the model of the router in question.
Steps to Hack WiFi Passwords
In addition to the aforementioned KisMAC application, you will also use a collection of Linux tools known as Aircrack-ng. You also need a password file that contains the actual password of the network you are attacking. Files containing thousands or millions of the most commonly used passwords are available for download on the Internet.